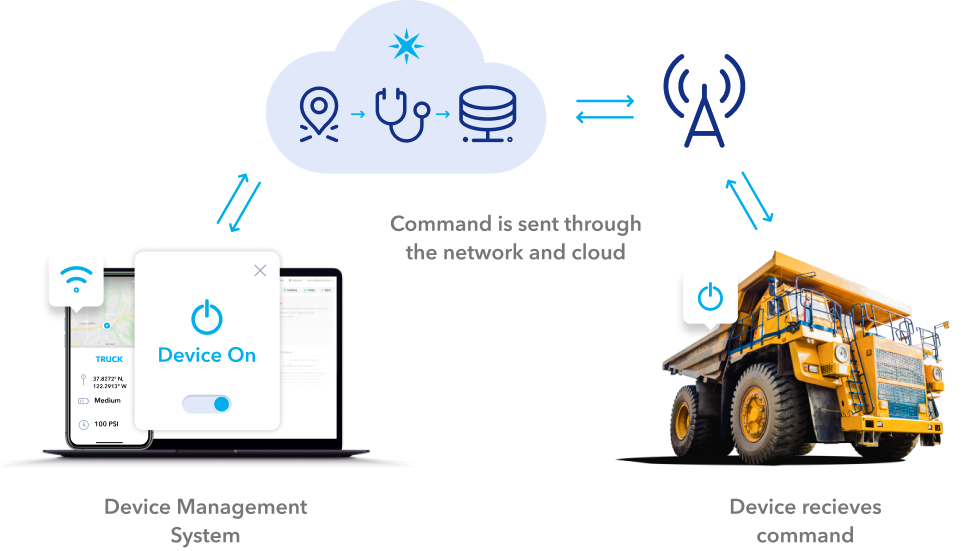
The Internet of Things (IoT) has revolutionized the way we interact with devices, enabling seamless connectivity and control from virtually anywhere. However, managing IoT remote control behind firewall systems presents unique challenges and opportunities. In this article, we will delve into the intricacies of IoT remote control within secure networks, offering practical solutions and expert insights.
As IoT devices become increasingly integrated into homes, businesses, and industries, ensuring secure remote access is paramount. Firewalls act as the first line of defense for network security, but they can also pose barriers to remote device control. Understanding how to navigate these obstacles is crucial for maintaining both functionality and safety.
This guide aims to provide a detailed exploration of IoT remote control behind firewall systems, offering actionable advice and addressing common concerns. Whether you're a tech enthusiast, a business owner, or an IT professional, this article will equip you with the knowledge to optimize your IoT setup securely.
Read also:How Much Does Jim Parsons Make On Young Sheldon
Table of Contents
- Introduction to IoT Remote Control Behind Firewall
- Understanding Firewalls and Their Role in IoT Security
- Challenges of IoT Remote Control Behind Firewall
- Solutions for Secure IoT Remote Control
- Using VPN for IoT Remote Control
- Exploring Port Forwarding
- Leveraging Cloud-Based Solutions
- Best Practices for Secure IoT Deployment
- Real-World Case Studies
- Future Trends in IoT Remote Control
- Conclusion and Call to Action
Introduction to IoT Remote Control Behind Firewall
IoT remote control behind firewall systems is a critical aspect of modern network management. With the proliferation of smart devices, users often require remote access to monitor and manage their IoT setups. However, firewalls are designed to restrict unauthorized access, creating a potential conflict between security and functionality.
Firewalls play a pivotal role in safeguarding networks by filtering incoming and outgoing traffic based on predetermined security rules. While this enhances security, it can complicate remote IoT device management. Striking a balance between accessibility and security is essential for effective IoT deployment.
In this section, we will explore the basics of IoT remote control and the importance of firewalls in securing networked environments. Understanding these foundational concepts is key to implementing secure and efficient IoT solutions.
Understanding Firewalls and Their Role in IoT Security
Firewalls are essential components of network security infrastructure. They act as gatekeepers, monitoring and controlling traffic flow between trusted internal networks and untrusted external networks, such as the internet. For IoT remote control behind firewall systems, understanding how firewalls operate is crucial.
Types of Firewalls
There are several types of firewalls, each with unique features and capabilities:
- Packet Filtering Firewalls: Analyze individual packets of data and allow or deny them based on predefined rules.
- Stateful Inspection Firewalls: Track active connections and use this information to make more informed decisions about traffic.
- Application-Level Gateways: Also known as proxy firewalls, they act as intermediaries between internal and external networks.
- Next-Generation Firewalls (NGFW): Incorporate advanced features such as deep packet inspection and intrusion prevention.
Selecting the appropriate firewall type depends on the specific needs of your IoT setup and the level of security required.
Read also:Good Morning Prayer For My Man
Challenges of IoT Remote Control Behind Firewall
Managing IoT remote control behind firewall systems presents several challenges that must be addressed to ensure both functionality and security. Below are some of the most common hurdles:
Security Risks
Opening ports or creating exceptions in firewalls to enable remote access can expose networks to potential threats. Hackers may exploit these vulnerabilities to gain unauthorized access to sensitive data or disrupt services.
Complexity
Configuring firewalls for IoT remote control can be complex, requiring a thorough understanding of network architecture and security protocols. Misconfigurations can lead to either excessive restrictions or insufficient protection.
Scalability
As IoT deployments grow, maintaining secure remote access for an increasing number of devices can become challenging. Ensuring that firewalls can scale effectively is essential for long-term success.
Solutions for Secure IoT Remote Control
To address the challenges of IoT remote control behind firewall systems, several solutions can be implemented. These strategies focus on enhancing security while maintaining accessibility.
Network Segmentation
Segmenting IoT devices into separate subnetworks can help isolate them from critical systems, reducing the risk of unauthorized access. This approach allows for more granular control over network traffic and enhances overall security.
Authentication and Authorization
Implementing robust authentication and authorization mechanisms ensures that only authorized users can access IoT devices remotely. Multi-factor authentication (MFA) and role-based access control (RBAC) are effective tools for achieving this.
Using VPN for IoT Remote Control
A Virtual Private Network (VPN) is a widely used solution for secure IoT remote control behind firewall systems. By creating an encrypted tunnel between devices and remote users, a VPN ensures that data transmitted over the internet remains private and secure.
Key benefits of using a VPN include:
- Enhanced data encryption
- Improved privacy
- Reduced risk of interception
However, it's important to choose a reputable VPN provider and configure it correctly to maximize its effectiveness.
Exploring Port Forwarding
Port forwarding is another method for enabling IoT remote control behind firewall systems. This technique involves directing incoming traffic from a specific external port to an internal device within the network.
While port forwarding can simplify remote access, it also introduces potential security risks. To mitigate these risks, it's crucial to:
- Use strong passwords for devices
- Limit access to specific IP addresses
- Regularly update firmware and software
Leveraging Cloud-Based Solutions
Cloud-based platforms offer an alternative approach to IoT remote control behind firewall systems. By hosting IoT devices and their management interfaces in the cloud, users can access them securely from anywhere without the need for complex firewall configurations.
Popular cloud providers such as AWS, Microsoft Azure, and Google Cloud offer robust IoT solutions with built-in security features. These platforms provide scalable infrastructure, automated updates, and advanced analytics capabilities.
Best Practices for Secure IoT Deployment
To ensure secure and efficient IoT remote control behind firewall systems, it's important to follow best practices. Below are some key recommendations:
- Regularly update device firmware and software
- Use strong, unique passwords for all devices
- Implement network segmentation and access control
- Monitor network traffic for suspicious activity
- Conduct regular security audits and assessments
By adhering to these guidelines, you can significantly enhance the security of your IoT deployment.
Real-World Case Studies
Examining real-world examples of IoT remote control behind firewall systems can provide valuable insights into best practices and potential pitfalls. Below are two case studies that highlight successful implementations:
Case Study 1: Smart Home Automation
A homeowner wanted to remotely control their smart home devices while maintaining a secure network. By implementing a combination of network segmentation, a VPN, and strong authentication measures, they achieved seamless remote access without compromising security.
Case Study 2: Industrial IoT
A manufacturing company sought to monitor and manage their IoT devices remotely. By leveraging cloud-based solutions and adhering to strict security protocols, they successfully implemented a secure and scalable IoT infrastructure.
Future Trends in IoT Remote Control
The landscape of IoT remote control behind firewall systems is continually evolving. Emerging technologies and trends are shaping the future of this field. Some notable developments include:
Edge Computing
Edge computing brings processing power closer to IoT devices, reducing latency and improving performance. This approach enhances the efficiency of remote control systems and minimizes reliance on centralized cloud infrastructure.
Artificial Intelligence and Machine Learning
AI and ML are increasingly being integrated into IoT solutions to enhance security and optimize performance. These technologies enable predictive analytics, anomaly detection, and automated decision-making.
Conclusion and Call to Action
In conclusion, mastering IoT remote control behind firewall systems requires a comprehensive understanding of both IoT technology and network security principles. By implementing the strategies and best practices outlined in this article, you can achieve secure and efficient remote access to your IoT devices.
We encourage readers to share their thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our site for further insights into IoT and related technologies. Together, let's build a safer and more connected future!