Remote SSH VNC access has become a crucial skill for IT professionals and remote workers alike. Whether you're managing servers, troubleshooting issues, or accessing files from a distant location, understanding how to navigate through firewalls is essential for seamless connectivity. This guide will delve into the nuances of remote SSH VNC setups, ensuring you can access your computer securely and efficiently.
In today's fast-paced digital world, the ability to access computers remotely is no longer a luxury but a necessity. Many organizations now rely on remote access tools to maintain productivity and ensure business continuity. However, with firewalls and network restrictions in place, achieving secure and stable connections can be challenging. This article aims to demystify the process by providing actionable insights and step-by-step instructions.
Our focus will be on remote SSH VNC setups, which combine the power of SSH tunnels and VNC protocols to bypass firewall restrictions. By the end of this guide, you'll have a comprehensive understanding of how to configure and manage these connections, ensuring your data remains secure while enabling unrestricted access to your remote systems.
Read also:Unique Small Arm Tattoos For Females
Table of Contents
- Introduction to Remote SSH VNC
- Understanding SSH and VNC Basics
- Firewall Challenges in Remote Access
- Setting Up SSH Tunnels
- Configuring VNC Clients and Servers
- Bypassing Firewalls with SSH Tunnels
- Security Best Practices for Remote Access
- Common Issues and Troubleshooting Tips
- Recommended Tools and Software
- Conclusion and Next Steps
Introduction to Remote SSH VNC
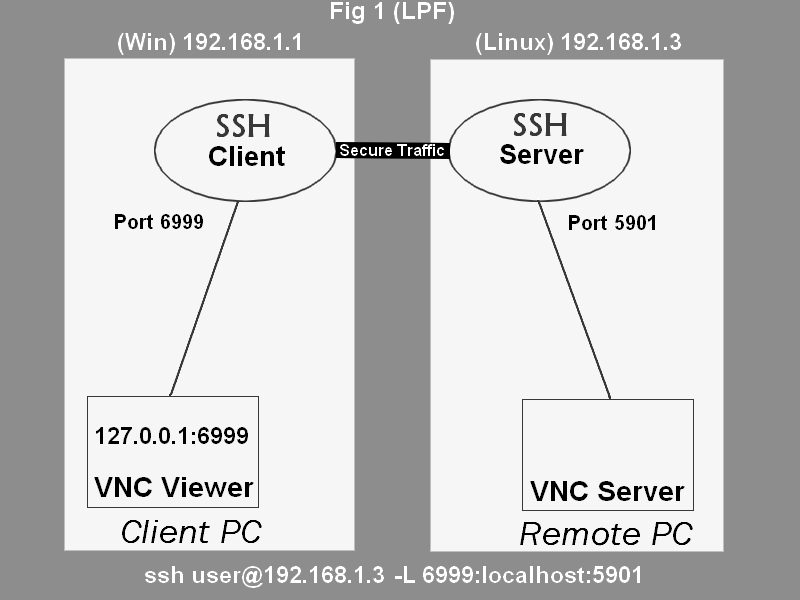
Remote SSH VNC access is a powerful technique that allows users to control computers located behind firewalls securely. SSH (Secure Shell) provides encrypted communication channels, while VNC (Virtual Network Computing) enables graphical remote desktop sharing. Together, they form a robust solution for accessing remote systems without compromising security.
Firewalls are designed to protect networks from unauthorized access, but they often block standard VNC ports. To overcome this limitation, SSH tunnels act as a bridge, encapsulating VNC traffic within encrypted SSH connections. This ensures that your data remains private and secure, even when traversing restrictive networks.
Whether you're a system administrator managing multiple servers or an individual needing remote access to your home computer, understanding how to configure SSH VNC connections is invaluable. This section will explore the fundamentals and benefits of this approach, setting the stage for more advanced configurations.
Understanding SSH and VNC Basics
What is SSH?
SSH, or Secure Shell, is a cryptographic network protocol used for secure communication over unsecured networks. It provides a secure channel for executing commands, transferring files, and managing remote systems. SSH encrypts all data transmitted between the client and server, ensuring confidentiality and integrity.
What is VNC?
VNC, or Virtual Network Computing, is a graphical desktop sharing system that allows users to remotely control another computer. It transmits keyboard and mouse events from the client to the server and sends screen updates in the opposite direction. VNC is platform-independent and works across various operating systems, making it a versatile tool for remote access.
By combining SSH and VNC, users can create secure tunnels for transmitting VNC traffic, effectively bypassing firewall restrictions and ensuring data privacy.
Read also:Happy Sunday To My Friends
Firewall Challenges in Remote Access
Firewalls are essential components of network security, designed to block unauthorized access and protect sensitive data. However, they can also pose challenges for remote access solutions like VNC, which rely on specific ports to function. Standard VNC ports (e.g., 5900-5909) are often blocked by corporate firewalls, preventing direct connections.
SSH tunnels offer a solution to this problem by encapsulating VNC traffic within encrypted SSH connections. Since SSH typically uses port 22, which is less likely to be blocked, it provides a reliable workaround for accessing computers behind firewalls. This section will explore common firewall configurations and how SSH tunnels can be used to overcome them.
Setting Up SSH Tunnels
Setting up an SSH tunnel involves configuring the client and server to establish a secure connection. Here's a step-by-step guide to help you get started:
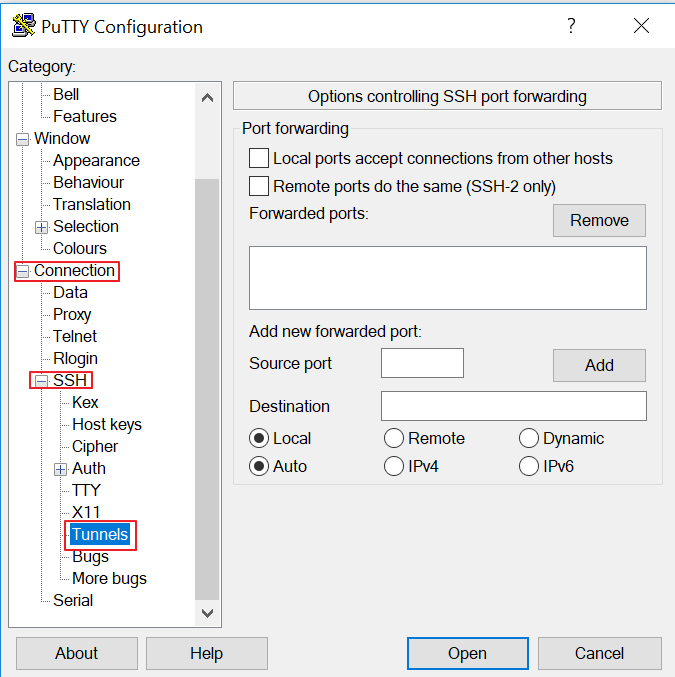
- Install an SSH client on your local machine (e.g., OpenSSH, PuTTY).
- Ensure that SSH is enabled on the remote server or computer.
- Open a terminal or command prompt and enter the following command:
ssh -L 5901:localhost:5901 user@remote-server. - Replace
userwith your username andremote-serverwith the IP address or domain name of the remote computer. - Enter your password or use an SSH key for authentication.
This command creates a local port forwarding tunnel, mapping port 5901 on your local machine to port 5901 on the remote server. You can now connect to the VNC server through this tunnel.
Configuring VNC Clients and Servers
VNC Server Setup
To configure a VNC server, follow these steps:
- Install a VNC server software on your remote computer (e.g., TightVNC, RealVNC, TigerVNC).
- Set a secure password for VNC authentication.
- Configure the server to listen on the desired port (e.g., 5901).
VNC Client Setup
On your local machine, install a VNC client and connect to localhost:5901 to access the remote desktop through the SSH tunnel. Popular VNC clients include:
- RealVNC Viewer
- TightVNC Viewer
- UltraVNC
Ensure that your VNC client supports encryption and authentication to maintain secure connections.
Bypassing Firewalls with SSH Tunnels
Firewalls often block standard VNC ports, making it difficult to establish direct connections. SSH tunnels provide a reliable solution by encapsulating VNC traffic within encrypted SSH connections. Since SSH typically uses port 22, which is less likely to be blocked, it allows VNC traffic to bypass firewall restrictions.
When configuring SSH tunnels, consider the following best practices:
- Use strong passwords or SSH keys for authentication.
- Enable encryption to protect data in transit.
- Monitor tunnel activity to detect unauthorized access.
By following these guidelines, you can ensure secure and stable connections even in restrictive network environments.
Security Best Practices for Remote Access
Security is paramount when configuring remote SSH VNC access. Here are some best practices to enhance the security of your connections:
- Use SSH keys instead of passwords for authentication.
- Enable two-factor authentication (2FA) for added security.
- Regularly update your SSH and VNC software to patch vulnerabilities.
- Limit access to trusted IP addresses or networks.
- Monitor logs for suspicious activity.
Implementing these measures will help protect your systems from unauthorized access and potential data breaches.
Common Issues and Troubleshooting Tips
Despite careful planning, issues may arise when configuring SSH VNC connections. Here are some common problems and their solutions:
- Connection Refused: Ensure that SSH and VNC services are running on the remote server.
- Authentication Failed: Verify your username, password, and SSH key settings.
- Slow Performance: Optimize your VNC settings for lower bandwidth connections.
- Firewall Blocks: Confirm that port 22 is open and not blocked by the firewall.
By addressing these issues promptly, you can maintain stable and secure remote access to your systems.
Recommended Tools and Software
Several tools and software can simplify the process of configuring SSH VNC connections. Here are some recommendations:
- OpenSSH: A free and open-source SSH client and server.
- TightVNC: A lightweight and efficient VNC server and client.
- RealVNC: A feature-rich VNC solution with enterprise-grade security.
- PuTTY: A popular SSH client for Windows users.
Choose the tools that best suit your needs and integrate them into your workflow for optimal results.
Conclusion and Next Steps
Remote SSH VNC access is a powerful technique that enables secure and efficient remote connections, even when firewalls are in place. By understanding the fundamentals of SSH and VNC, configuring SSH tunnels, and implementing security best practices, you can ensure seamless access to your remote systems.
We encourage you to explore the resources mentioned in this guide and experiment with different tools and configurations. Your feedback and questions are invaluable, so feel free to leave a comment or share this article with others who may benefit from it. For more in-depth information, consider reading our related articles on network security and remote access solutions.