In today's interconnected world, using RemoteIoT behind a firewall is a challenge many businesses and developers face. Whether it's for monitoring industrial equipment, managing smart home devices, or enhancing IoT network security, understanding how to work with RemoteIoT in a restricted environment is crucial. In this article, we will explore effective strategies, tools, and best practices to help you navigate this complex landscape.
As the Internet of Things (IoT) continues to expand, the need for secure communication becomes increasingly important. Firewalls are often implemented to protect networks from unauthorized access, but they can also create barriers for IoT devices trying to connect to external systems. Learning how to use RemoteIoT behind firewall using the right techniques is essential for maintaining both security and functionality.
This guide will provide comprehensive insights into configuring RemoteIoT systems, ensuring seamless communication while adhering to strict security protocols. Whether you're a developer, IT professional, or someone interested in IoT technology, this article will equip you with the knowledge to overcome common challenges associated with firewalls and IoT integration.
Read also:Adult Friday Jokes
Table of Contents
- Introduction to RemoteIoT
- Understanding Firewalls
- Challenges of Using RemoteIoT Behind Firewall
- Methods to Use RemoteIoT Behind Firewall
- Port Forwarding
- VPN Solutions
- Cloud-Based Solutions
- Security Considerations
- Best Practices for RemoteIoT Deployment
- The Future of RemoteIoT Behind Firewalls
Introduction to RemoteIoT
RemoteIoT refers to the ability to control, monitor, and interact with IoT devices remotely. This technology has revolutionized industries by enabling real-time data collection and analysis from distant locations. However, when these devices are placed behind firewalls, their functionality can be restricted due to security policies.
To effectively use RemoteIoT behind firewall using the right methods, it's important to understand the basics of IoT architecture and how firewalls impact network communication. By leveraging advanced networking techniques, you can ensure that your IoT devices remain connected and operational without compromising security.
Understanding Firewalls
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Firewalls act as a barrier between trusted internal networks and untrusted external networks, such as the internet.
There are different types of firewalls, including packet-filtering, stateful inspection, proxy, and next-generation firewalls. Each type has its own advantages and limitations, and choosing the right firewall depends on the specific needs of your network.
How Firewalls Impact IoT Devices
IoT devices often require constant communication with external servers for data transmission and updates. Firewalls can block these communications if they are not properly configured, leading to connectivity issues and reduced functionality.
Challenges of Using RemoteIoT Behind Firewall
Using RemoteIoT behind firewall using traditional methods can present several challenges. These include restricted access, limited bandwidth, and potential security vulnerabilities. Here are some common obstacles:
Read also:Nidal Wonder New Girlfriend
- Restricted Access: Firewalls may block incoming and outgoing connections, preventing IoT devices from communicating with external servers.
- Bandwidth Limitations: High data transfer requirements can overwhelm firewall resources, leading to slow performance.
- Security Concerns: Opening ports or creating exceptions in the firewall can expose the network to potential threats.
Methods to Use RemoteIoT Behind Firewall
There are several methods to overcome the challenges of using RemoteIoT behind firewall using advanced techniques. Below, we explore some of the most effective strategies:
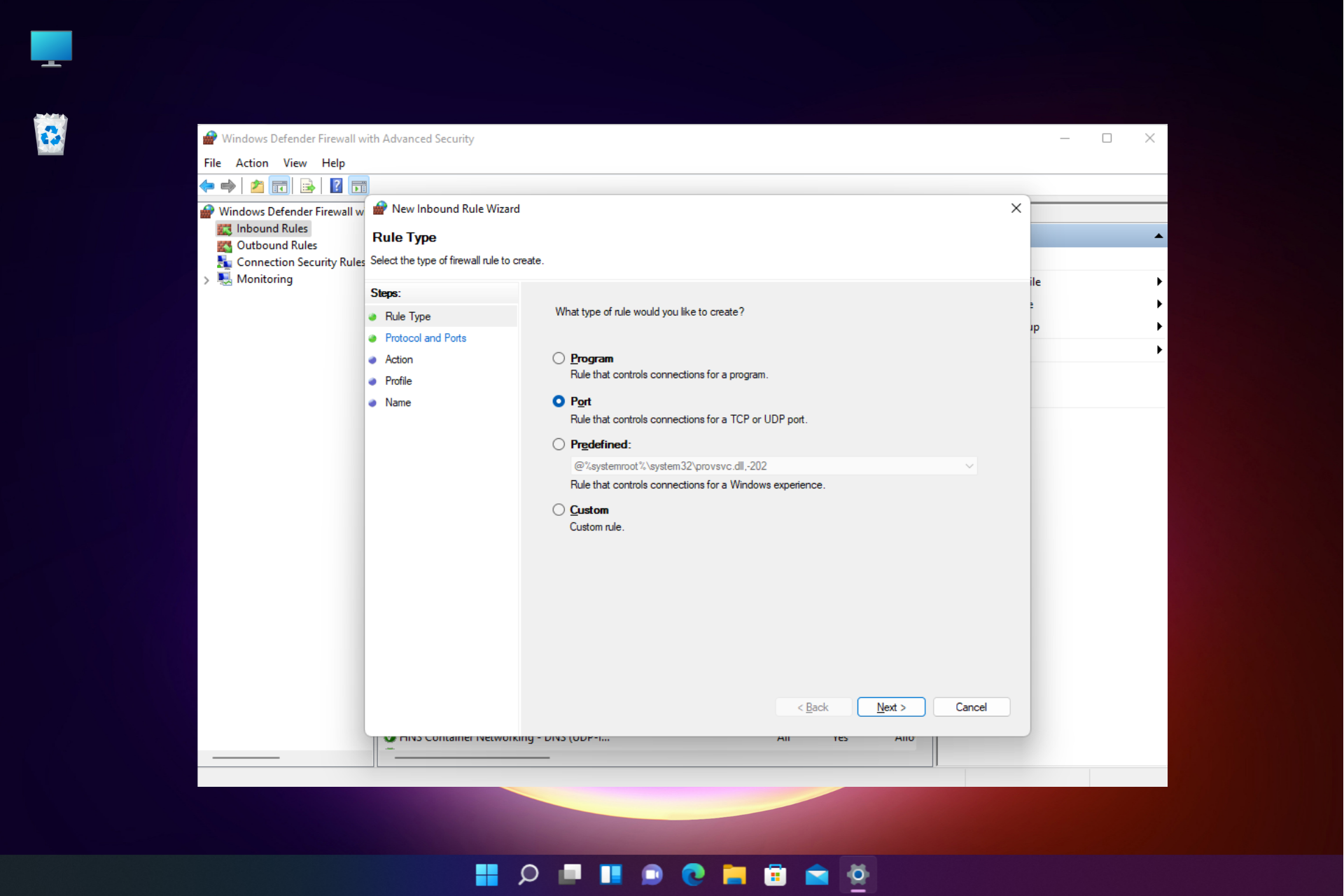
Port Forwarding
Port forwarding is a technique that allows external devices to connect to internal devices by mapping specific ports on the firewall to internal IP addresses. This method is commonly used to enable remote access to IoT devices without compromising security.
VPN Solutions
Virtual Private Networks (VPNs) create secure, encrypted tunnels between devices and networks, allowing IoT devices to communicate securely behind firewalls. This approach is ideal for organizations requiring high levels of security.
Cloud-Based Solutions
Cloud-based solutions provide a scalable and flexible way to manage IoT devices behind firewalls. By leveraging cloud platforms, organizations can centralize device management and data storage, reducing the burden on local firewalls.
Port Forwarding
Port forwarding is a powerful technique for enabling remote access to IoT devices behind firewalls. By configuring specific ports on the firewall to forward traffic to internal devices, you can maintain secure communication while avoiding the need to open all ports.
Key considerations when implementing port forwarding include:
- Identifying the necessary ports for IoT device communication.
- Configuring the firewall to allow only specific IP addresses and devices.
- Regularly monitoring and updating firewall rules to ensure security.
VPN Solutions
VPNs offer a secure and reliable way to use RemoteIoT behind firewall using encrypted connections. By establishing a virtual private network, you can protect sensitive data and ensure that all communication between devices remains confidential.
Popular VPN solutions for IoT include:
- OpenVPN
- WireGuard
- IPsec
Cloud-Based Solutions
Cloud-based platforms provide a robust infrastructure for managing IoT devices behind firewalls. These solutions offer features such as device registration, data analytics, and remote monitoring, all while maintaining high levels of security.
Advantages of cloud-based solutions include:
- Scalability: Easily add or remove devices as needed.
- Centralized Management: Simplify device management from a single dashboard.
- Enhanced Security: Leverage advanced encryption and authentication protocols.
Security Considerations
When using RemoteIoT behind firewall using any method, it's crucial to prioritize security. Below are some key security considerations:
- Encryption: Ensure all data transmissions are encrypted to prevent unauthorized access.
- Authentication: Implement strong authentication mechanisms to verify device and user identities.
- Regular Updates: Keep firmware and software up to date to address potential vulnerabilities.
Best Practices for RemoteIoT Deployment
Deploying RemoteIoT behind firewall using best practices can significantly improve performance and security. Here are some recommendations:
- Conduct a thorough risk assessment before implementing any solution.
- Choose the right firewall type based on your network requirements.
- Monitor network traffic regularly to detect and respond to potential threats.
- Train employees on the importance of cybersecurity and best practices.
The Future of RemoteIoT Behind Firewalls
As IoT technology continues to evolve, the future of RemoteIoT behind firewalls looks promising. Advancements in artificial intelligence, machine learning, and blockchain technology are expected to enhance security and functionality.
Organizations that embrace these innovations will be better equipped to navigate the complexities of IoT deployment while maintaining robust security measures. By staying informed and proactive, you can ensure that your RemoteIoT systems remain secure and efficient.
Kesimpulan
In conclusion, using RemoteIoT behind firewall using the right techniques and tools is essential for maintaining secure and functional IoT networks. By understanding the challenges and implementing effective strategies, you can overcome common obstacles and achieve optimal performance.
We encourage you to share your thoughts and experiences in the comments below. Additionally, explore our other articles for more insights into IoT technology and network security. Together, we can build a safer and more connected future.