Learning how to access and manage remote IoT devices via SSH is a crucial skill in today's interconnected world. As the Internet of Things (IoT) continues to grow, the ability to remotely control and monitor devices becomes increasingly important for both professionals and hobbyists. Whether you're managing home automation systems or large-scale industrial networks, understanding SSH (Secure Shell) is essential. This tutorial will guide you step-by-step through the process of setting up, configuring, and troubleshooting SSH connections for remote IoT devices.
In this article, we will explore the basics of SSH, its importance in IoT ecosystems, and provide practical examples to help you master remote access techniques. By the end of this guide, you'll be equipped with the knowledge and skills necessary to securely connect to and manage your remote IoT devices.
Our focus will be on delivering actionable insights while ensuring that the content aligns with best practices for security and efficiency. Let's dive in and discover how SSH can revolutionize the way you interact with your IoT devices.
Read also:Freaky Quotes Funny For Instagram
Table of Contents
- What is SSH?
- Why SSH is Important for IoT Devices
- Setting Up SSH on Remote IoT Devices
- Connecting to RemoteIoT Devices via SSH
- Security Best Practices for SSH
- Troubleshooting Common SSH Issues
- Automating SSH Connections
- Advanced Features of SSH for IoT
- Useful Tools for SSH Management
- Conclusion and Next Steps
What is SSH?
SSH, or Secure Shell, is a cryptographic network protocol designed to provide secure communication over unsecured networks. It is widely used for remote command-line login and execution of commands on networked computers. For remote IoT device management, SSH ensures that data exchanged between your local machine and the IoT device remains encrypted and protected from unauthorized access.
Understanding SSH is fundamental for anyone working with remoteIoT devices. The protocol not only facilitates secure communication but also offers features like file transfer, port forwarding, and tunneling, which are invaluable in IoT applications.
SSH operates on port 22 by default and uses public-key cryptography to authenticate users and encrypt data. This makes it an ideal choice for secure remote access in environments where security and reliability are paramount.
Why SSH is Important for IoT Devices
In the context of IoT, SSH plays a critical role in ensuring secure communication between devices and their remote management interfaces. As IoT devices often operate in open or unsecured networks, the risk of unauthorized access and data breaches is significant. SSH mitigates these risks by providing a secure channel for communication.
Here are some reasons why SSH is indispensable for remoteIoT device management:
- Encryption: SSH encrypts all data transmitted between the client and server, preventing eavesdropping and data theft.
- Authentication: It supports multiple authentication methods, including password-based and public-key authentication, ensuring only authorized users can access the devices.
- Reliability: SSH connections are robust and can handle interruptions gracefully, making them suitable for IoT devices that may operate in challenging environments.
With the increasing reliance on IoT technologies, mastering SSH is not just an advantage—it's a necessity.
Read also:Happy Sunday To My Friends
Setting Up SSH on Remote IoT Devices
Raspberry Pi Example
One of the most popular IoT platforms is the Raspberry Pi, and setting up SSH on this device is straightforward. Follow these steps to enable SSH on a Raspberry Pi:
- Connect your Raspberry Pi to a monitor and keyboard or access it via another computer.
- Open the terminal and type the following command to enable SSH:
sudo raspi-config. - Navigate to the "Interfacing Options" menu and select "SSH".
- Choose "Yes" to enable SSH and then exit the configuration tool.
- Reboot your Raspberry Pi to apply the changes.
Once SSH is enabled, you can connect to your Raspberry Pi from any remote location using an SSH client. This setup is applicable to most Linux-based IoT devices, with minor variations depending on the operating system.
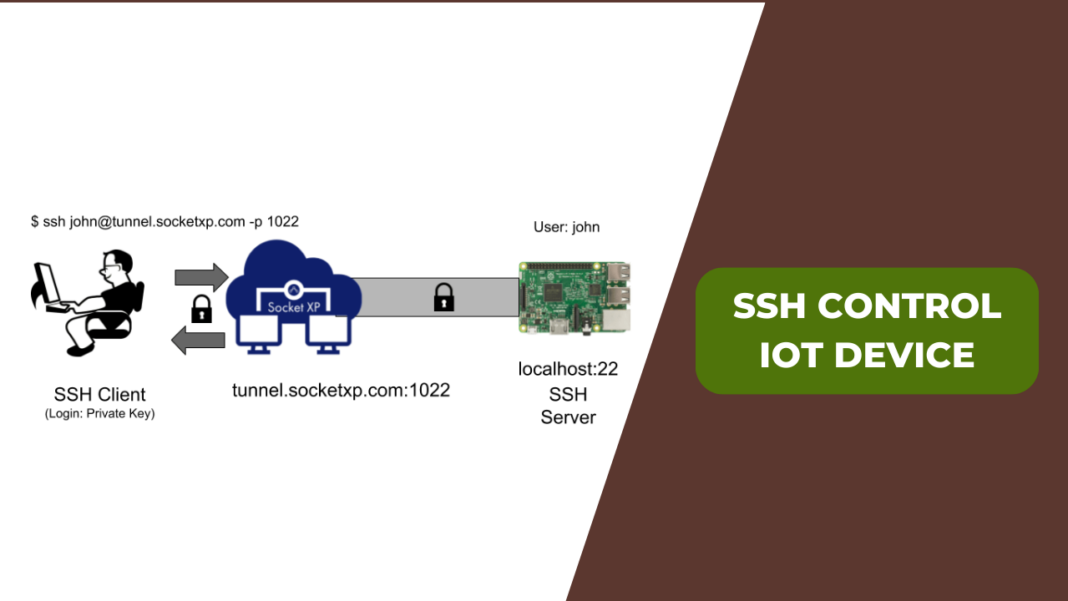
Connecting to RemoteIoT Devices via SSH
Connecting to your remote IoT devices via SSH is a simple process once the server-side configuration is complete. Here's how you can establish a connection:
- Open an SSH client on your local machine. Popular options include PuTTY for Windows and the built-in terminal for macOS and Linux.
- Enter the command:
ssh username@ip_address, replacing "username" with the actual username of the remote device and "ip_address" with its IP address. - When prompted, enter the password for the user account or use a private key for authentication.
Upon successful authentication, you will be logged into the remote device and can execute commands as needed. This method provides a secure and efficient way to manage your IoT devices remotely.
Security Best Practices for SSH
While SSH is inherently secure, there are additional measures you can take to enhance its security:
- Disable Password Authentication: Use public-key authentication instead to reduce the risk of brute-force attacks.
- Change Default Port: Modify the default SSH port (22) to a non-standard port to deter automated attacks.
- Use Firewall Rules: Restrict SSH access to specific IP addresses or ranges using firewall rules.
- Regularly Update Software: Keep your SSH server and related software up to date to patch vulnerabilities.
Implementing these best practices will significantly improve the security posture of your remoteIoT device management.
Troubleshooting Common SSH Issues
Even with proper configuration, you may encounter issues when using SSH. Here are some common problems and their solutions:
- Connection Refused: Ensure the SSH service is running on the remote device and that the firewall allows incoming connections on the SSH port.
- Authentication Failed: Verify that the username and password are correct or that the public key is properly installed on the server.
- Timeout Errors: Check the network connection and ensure there are no routing issues between the client and server.
By addressing these issues systematically, you can resolve most SSH-related problems effectively.
Automating SSH Connections
Automating SSH connections can save time and reduce the risk of human error. Tools like SSH keys, cron jobs, and scripts can be used to streamline repetitive tasks. For example, you can set up a script to automatically back up files from your remoteIoT devices at regular intervals.
Additionally, consider using configuration management tools like Ansible or Puppet to automate the deployment and management of SSH configurations across multiple devices.
Advanced Features of SSH for IoT
Port Forwarding
SSH port forwarding allows you to securely access services running on remoteIoT devices by forwarding specific ports through the encrypted SSH connection. This is particularly useful for accessing web interfaces or databases hosted on the device without exposing them directly to the internet.
SSH Tunneling
SSH tunneling creates a secure channel through which other protocols can pass. This is ideal for securely accessing applications or services that do not natively support encryption. For instance, you can use SSH tunneling to securely access a MySQL database running on a remoteIoT device.
Useful Tools for SSH Management
Several tools can enhance your SSH experience and simplify remoteIoT device management:
- SSHFS: Allows you to mount remote file systems over SSH, providing seamless access to files on your IoT devices.
- mosh: A mobile shell that improves upon SSH by handling intermittent connectivity better, making it ideal for mobile or unreliable networks.
- Keychain: Helps manage SSH keys and passwords across multiple sessions, reducing the need to repeatedly authenticate.
Exploring these tools can further enhance your ability to manage remoteIoT devices efficiently.
Conclusion and Next Steps
This comprehensive remoteIoT device SSH tutorial has covered everything from the basics of SSH to advanced features and best practices. By following the steps outlined in this guide, you can confidently manage your IoT devices remotely while maintaining a high level of security.
We encourage you to put this knowledge into practice by setting up SSH on your own IoT devices and exploring the various tools and techniques discussed. Don't forget to share your experiences and insights in the comments section below. Additionally, consider exploring other articles on our site for more in-depth coverage of IoT-related topics.
Thank you for reading, and happy hacking!