Remotely accessing your Raspberry Pi has become an essential skill for developers, hobbyists, and tech enthusiasts in the IoT (Internet of Things) era. Whether you're managing a home automation system or working on a remote IoT project, understanding how to securely connect to your Raspberry Pi from anywhere in the world is crucial. This article will guide you step-by-step through the process, ensuring you have the knowledge and tools to set up a reliable remote connection.
As more devices become interconnected, the demand for remote access solutions continues to grow. From monitoring environmental sensors to controlling smart home devices, having the ability to interact with your Raspberry Pi remotely opens up endless possibilities. However, setting up remote access requires careful planning and adherence to security best practices to avoid potential risks.
In this RemoteIoT tutorial, we'll explore various methods and tools that allow you to access your Raspberry Pi securely. By the end of this guide, you'll have the confidence to manage your Raspberry Pi remotely, whether you're across the room or on the other side of the world. Let's dive in!
Read also:Bella Grace Weems Religion
Table of Contents
- Introduction to Remote Access
- Raspberry Pi Overview
- Understanding SSH Basics
- Setting Up SSH on Raspberry Pi
- Ensuring a Secure Connection
- Using a VPN for Enhanced Security
- Remote Desktop Solutions
- Cloud-Based Solutions for Remote Access
- Troubleshooting Common Issues
- Conclusion and Next Steps
Introduction to Remote Access
Remote access to a Raspberry Pi enables users to interact with their device without being physically present. This functionality is particularly useful for IoT projects, server management, and monitoring systems. By leveraging tools like SSH, VNC, and cloud platforms, you can efficiently control your Raspberry Pi from any location.
Why Remote Access Matters
Remote access is not just a convenience; it's a necessity for modern IoT applications. Whether you're managing a fleet of sensors or maintaining a home automation system, the ability to troubleshoot and update your Raspberry Pi remotely saves time and resources. Additionally, remote access allows for collaboration with team members who may be located elsewhere.
Raspberry Pi Overview
The Raspberry Pi is a versatile single-board computer that has revolutionized the maker community. Known for its affordability and flexibility, it serves as the foundation for countless IoT projects. Understanding its capabilities and limitations is essential for setting up remote access effectively.
Key Features of Raspberry Pi
- Compact size and low power consumption
- Support for multiple operating systems
- Built-in connectivity options (Wi-Fi, Bluetooth, Ethernet)
- Extensive community support and resources
Understanding SSH Basics
SSH (Secure Shell) is a protocol that allows secure communication between devices over an unsecured network. It provides a command-line interface for managing remote systems and is widely used for Raspberry Pi remote access.
Advantages of Using SSH
- Encrypted communication for enhanced security
- Lightweight and efficient
- Supports file transfer via SCP/SFTP
Setting Up SSH on Raspberry Pi
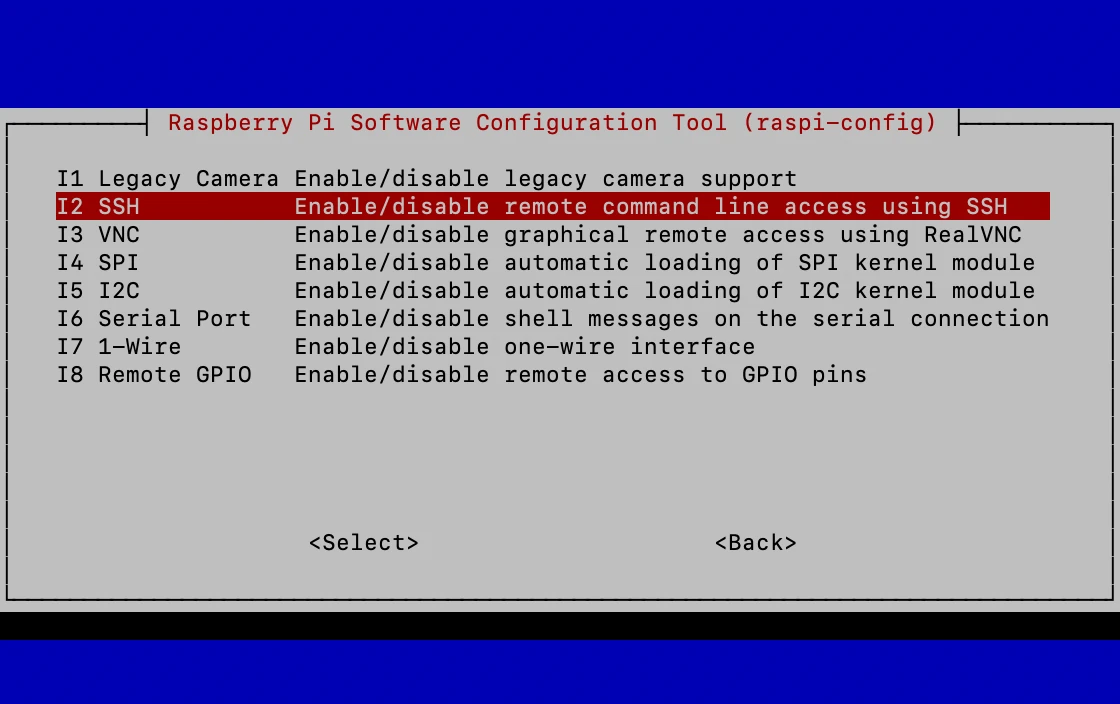
Enabling SSH on your Raspberry Pi is a straightforward process. Follow these steps to configure SSH on your device:
Step-by-Step Guide
- Ensure your Raspberry Pi is connected to the internet.
- Access the Raspberry Pi Configuration tool by typing
sudo raspi-configin the terminal. - Navigate to "Interfacing Options" and enable SSH.
- Reboot your Raspberry Pi to apply the changes.
Ensuring a Secure Connection
Security should always be a top priority when setting up remote access. Implementing best practices such as using strong passwords, enabling two-factor authentication, and regularly updating your system can significantly reduce the risk of unauthorized access.
Read also:Crescent University Nigeria
Best Practices for Security
- Use complex passwords and avoid common patterns.
- Disable password-based authentication in favor of SSH keys.
- Regularly update your Raspberry Pi's software to patch vulnerabilities.
Using a VPN for Enhanced Security
A Virtual Private Network (VPN) adds an additional layer of security to your remote access setup. By encrypting all traffic between your device and the Raspberry Pi, a VPN ensures that sensitive data remains protected from potential eavesdroppers.
Popular VPN Solutions
- WireGuard
- OpenVPN
- Tailscale
Remote Desktop Solutions
While SSH is ideal for command-line tasks, some users may prefer a graphical interface for interacting with their Raspberry Pi. Remote desktop solutions like VNC (Virtual Network Computing) provide this functionality, allowing you to control your Raspberry Pi as if you were sitting in front of it.
Setting Up VNC on Raspberry Pi
To enable VNC on your Raspberry Pi, follow these steps:
- Install the VNC Server by typing
sudo apt install realvnc-vnc-serverin the terminal. - Enable VNC through the Raspberry Pi Configuration tool.
- Download the VNC Viewer app on your client device and connect using the Raspberry Pi's IP address.
Cloud-Based Solutions for Remote Access
Cloud platforms offer an alternative approach to remote access by hosting your Raspberry Pi's services on the internet. This method eliminates the need for port forwarding and complex network configurations, making it easier for beginners to set up remote access.
Advantages of Cloud-Based Solutions
- Easy setup with minimal technical knowledge required.
- Access from any device with an internet connection.
- Automatic updates and security patches.
Troubleshooting Common Issues
Even with careful planning, issues can arise when setting up remote access. Below are some common problems and their solutions:
Problem: Unable to Connect via SSH
- Check that SSH is enabled on your Raspberry Pi.
- Verify the IP address and ensure there are no network conflicts.
- Ensure that firewalls or routers are not blocking the SSH port (default is 22).
Conclusion and Next Steps
Remotely accessing your Raspberry Pi is a powerful capability that enhances the functionality of your IoT projects. By following the steps outlined in this RemoteIoT tutorial, you can set up a secure and reliable connection to your device from anywhere in the world. Remember to prioritize security and regularly update your system to protect against potential threats.
We encourage you to experiment with the tools and techniques discussed in this article. Leave a comment below to share your experiences or ask questions. For more in-depth guides and tutorials, explore our other articles and resources. Together, let's build a smarter, more connected world!
References: