Managing IoT devices remotely has become a critical skill in today's interconnected world. As more businesses and individuals rely on IoT technology, understanding how to use SSH (Secure Shell) to connect and manage these devices remotely is essential. This tutorial will guide you through the process step-by-step, ensuring you can confidently access and configure your IoT devices from anywhere.
In this article, we will delve into the intricacies of SSH remote IoT device management. Whether you're a beginner or someone looking to enhance your skills, this tutorial is designed to provide actionable insights. By the end of this guide, you'll have the tools and knowledge necessary to secure your IoT infrastructure effectively.
SSH remote IoT device management is not just about connecting to devices; it's about ensuring data security, optimizing performance, and maintaining control over your network. This tutorial will cover everything from basic setup to advanced configurations, ensuring you're equipped to handle any challenge that arises.
Read also:Famous People S Phone Numbers To Prank Call
Table of Contents
- Introduction to SSH
- IoT Device Overview
- Setting Up an SSH Server
- Connecting to a Remote IoT Device
- Securing Your SSH Connection
- Troubleshooting Common Issues
- Advanced SSH Features for IoT
- Best Practices for SSH Remote IoT Management
- Real-World Applications of SSH in IoT
- The Future of SSH in IoT Devices
Introduction to SSH
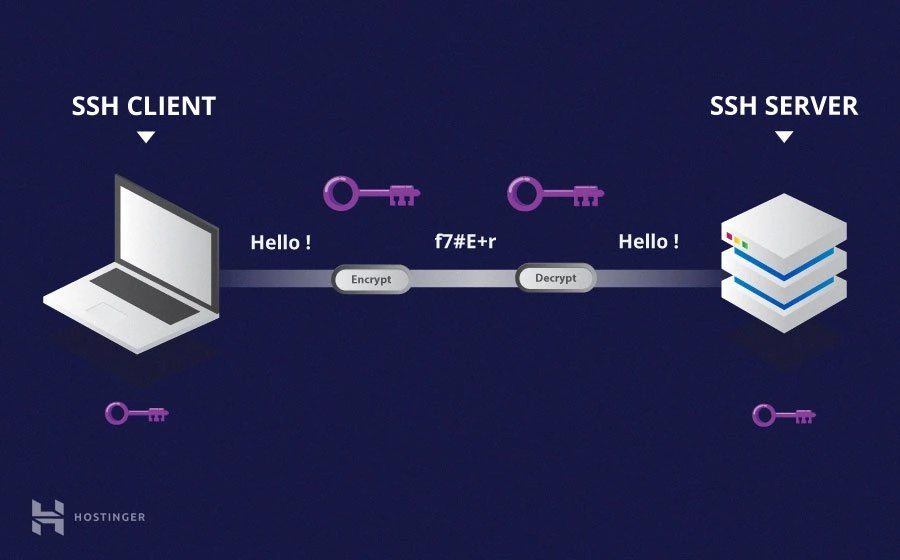
SSH, or Secure Shell, is a cryptographic network protocol used for secure communication between devices over an unsecured network. It provides a robust framework for remote device management, making it ideal for IoT applications where security is paramount.
In the context of IoT, SSH allows users to connect to remote devices securely, execute commands, and transfer files without exposing sensitive information to potential threats. By leveraging SSH, administrators can manage their IoT devices efficiently, ensuring they remain operational and secure.
Some key benefits of using SSH for IoT devices include:
- Encryption of all transmitted data
- Authentication mechanisms to prevent unauthorized access
- Support for secure file transfers via SCP and SFTP
IoT Device Overview
What Are IoT Devices?
IoT (Internet of Things) devices refer to any physical objects embedded with sensors, software, and connectivity capabilities, enabling them to collect and exchange data. These devices range from simple home automation systems to complex industrial machinery, all interconnected through the internet.
Common Types of IoT Devices
Here are some common types of IoT devices you might encounter:
- Smart thermostats
- Wearable health monitors
- Industrial sensors
- Smart home security systems
Each of these devices requires secure remote management, and SSH provides the necessary tools to achieve this.
Read also:Famous People Delaware
Setting Up an SSH Server
Before you can connect to your IoT device remotely, you need to set up an SSH server on the device itself. This involves installing the necessary software and configuring the server settings.
For Linux-based IoT devices, the process typically involves the following steps:
- Install the OpenSSH server package
- Configure the SSH server settings in the
/etc/ssh/sshd_configfile - Restart the SSH service to apply changes
Ensure that your device's firewall settings allow incoming SSH connections on port 22 (or a custom port if specified).
Connecting to a Remote IoT Device
Using SSH Clients
To connect to your IoT device remotely, you'll need an SSH client. Popular options include:
- Terminal on macOS and Linux
- PuTTY on Windows
The basic syntax for connecting to an IoT device via SSH is:
ssh [username]@[device-ip-address]
Replace [username] with your IoT device's username and [device-ip-address] with the device's IP address.
Securing Your SSH Connection
Securing your SSH connection is crucial to protect your IoT devices from unauthorized access. Here are some best practices:
- Use strong, unique passwords or public-key authentication
- Disable root login to prevent direct access to privileged accounts
- Change the default SSH port to a non-standard port
- Implement IP whitelisting to restrict access to trusted IP addresses
By following these practices, you can significantly enhance the security of your SSH connections.
Troubleshooting Common Issues
Connection Refused
If you encounter a "Connection refused" error, ensure that:
- The SSH server is running on the IoT device
- The device's firewall allows incoming SSH connections
- You're using the correct IP address and port number
Authentication Failed
Authentication failures can occur due to:
- Incorrect username or password
- Public key authentication issues
- Misconfigured SSH server settings
Review your credentials and server configuration to resolve these issues.
Advanced SSH Features for IoT
Tunneling and Port Forwarding
SSH tunneling allows you to securely forward traffic between your local machine and a remote IoT device. This is particularly useful for accessing services running on the device without exposing them directly to the internet.
SSH Keys for Automation
Using SSH keys for authentication can streamline remote management tasks, especially in automated environments. By setting up key-based authentication, you can eliminate the need for manual password entry.
Best Practices for SSH Remote IoT Management
To ensure effective and secure management of your IoT devices using SSH, consider the following best practices:
- Regularly update your IoT device's firmware and SSH server software
- Monitor SSH logs for suspicious activity
- Implement multi-factor authentication for added security
- Document your SSH configurations and procedures for future reference
By adhering to these practices, you can maintain a secure and efficient IoT infrastructure.
Real-World Applications of SSH in IoT
SSH plays a vital role in various real-world IoT applications, including:
- Remote monitoring and control of industrial equipment
- Secure data collection from environmental sensors
- Management of smart home devices
These applications demonstrate the versatility and importance of SSH in modern IoT ecosystems.
The Future of SSH in IoT Devices
As IoT technology continues to evolve, the role of SSH in securing remote connections will become even more critical. Emerging trends such as quantum-resistant cryptography and AI-driven security measures promise to enhance the security of SSH-based IoT management.
Staying informed about these advancements and adapting your practices accordingly will ensure your IoT infrastructure remains secure and efficient in the future.
Conclusion
In conclusion, mastering SSH remote IoT device management is essential for anyone working with IoT technology. By following the steps outlined in this tutorial, you can securely connect to and manage your IoT devices from anywhere in the world.
We encourage you to share your thoughts and experiences in the comments section below. Additionally, explore our other articles for more insights into IoT and related technologies. Together, let's build a safer and more connected future!
Data Source: SSH.com | Linux.com | IoT For All