Using RemoteIoT behind a firewall on a Mac is a challenge that many professionals face, especially when working remotely. With the increasing demand for secure access to IoT devices, understanding the best practices and tools is essential. In this article, we will explore step-by-step methods to configure RemoteIoT on a Mac while ensuring your network remains secure.
Whether you're a developer, IT professional, or hobbyist, accessing IoT devices remotely can streamline your workflow. However, firewalls often pose obstacles that make this process more complex. This guide will walk you through the necessary steps to bypass these barriers effectively.
By the end of this article, you will have a comprehensive understanding of how to configure RemoteIoT behind a firewall on your Mac, ensuring both functionality and security. Let's dive in!
Read also:The Rookie Ripper Actor
Table of Contents
- Introduction to RemoteIoT and Firewalls
- Understanding Firewalls and Their Role
- Mac Firewall: Features and Configurations
- What is RemoteIoT?
- Step-by-Step Setup Process
- Security Best Practices
- Troubleshooting Common Issues
- Tools and Software Recommendations
- Optimizing Performance
- Conclusion
Introduction to RemoteIoT and Firewalls
RemoteIoT has become an essential tool for managing and monitoring Internet of Things (IoT) devices from anywhere in the world. However, when working behind a firewall, especially on a Mac, the process can become complicated. A firewall is a security system designed to prevent unauthorized access to or from a private network. It acts as a barrier between your internal network and the internet, protecting sensitive data and systems.
For Mac users, the built-in firewall provides robust security features, but it can also block legitimate traffic if not configured correctly. This article will help you navigate these challenges by providing a detailed guide on how to use RemoteIoT behind a firewall on a Mac without compromising security.
Understanding Firewalls and Their Role
What is a Firewall?
A firewall is a network security device that monitors incoming and outgoing network traffic and permits or blocks data packets based on a set of security rules. Its primary purpose is to establish a barrier between internal networks and external sources, ensuring only authorized traffic can pass through.
Types of Firewalls
- Packet Filtering Firewalls: Inspect packets at the network layer and filter them based on predefined rules.
- Stateful Inspection Firewalls: Monitor active connections and make decisions based on the context of the traffic.
- Application-Level Gateways: Also known as proxy firewalls, these analyze traffic at the application layer, providing more granular control.
Mac Firewall: Features and Configurations
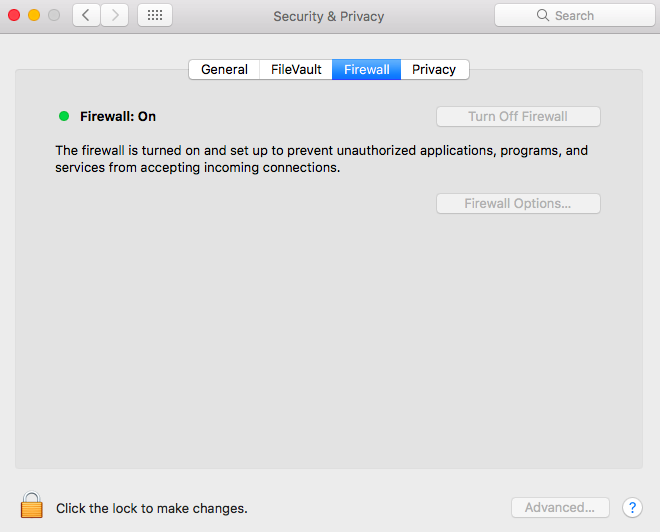
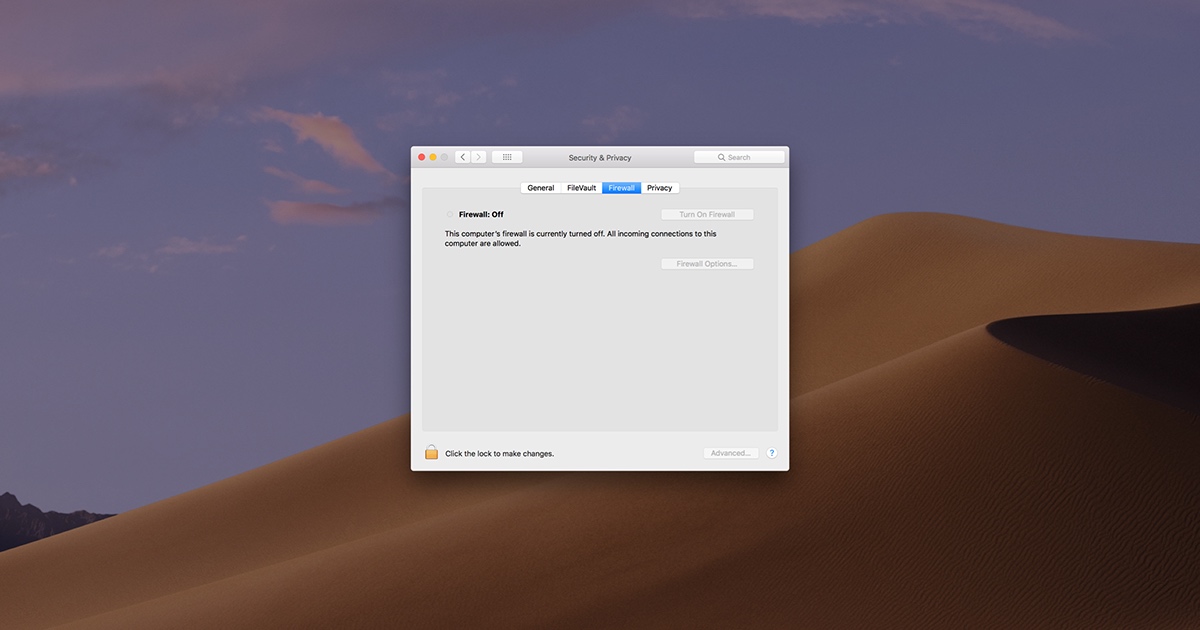
The Mac operating system comes equipped with a built-in firewall that offers several features to enhance network security. By default, the firewall is disabled, but you can enable it through the System Preferences.
How to Enable the Firewall on a Mac
- Go to System Preferences > Security & Privacy.
- Select the Firewall tab and click "Turn On Firewall."
- For advanced settings, click on "Firewall Options" and configure rules as needed.
What is RemoteIoT?
RemoteIoT is a software solution designed to facilitate remote access to IoT devices. It allows users to monitor, manage, and control IoT devices from anywhere in the world. Whether you're managing a smart home system or overseeing industrial equipment, RemoteIoT provides the tools you need to stay connected.
Key Features of RemoteIoT
- Secure remote access to IoT devices.
- Real-time monitoring and data visualization.
- Automated alerts and notifications.
Step-by-Step Setup Process
Step 1: Install RemoteIoT on Your Mac
Begin by downloading and installing the RemoteIoT software on your Mac. Ensure you are downloading from an official and trusted source to avoid security risks.
Read also:Bianca Kajlich Body
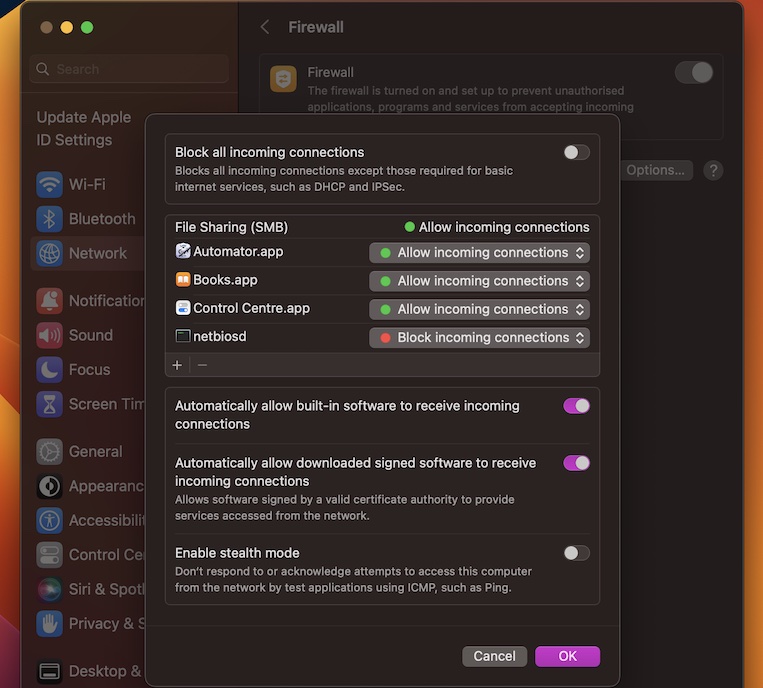
Step 2: Configure Firewall Rules
Once the software is installed, you need to configure your Mac's firewall to allow RemoteIoT traffic. This involves creating specific rules that permit incoming and outgoing connections for the RemoteIoT application.
Step 3: Test the Connection
After configuring the firewall, test the connection to ensure RemoteIoT can communicate with your IoT devices. Use diagnostic tools to verify that the connection is stable and secure.
Security Best Practices
While configuring RemoteIoT behind a firewall, it's crucial to follow security best practices to protect your network and devices. Below are some recommendations:
- Use Strong Passwords: Ensure all accounts and devices are protected with strong, unique passwords.
- Enable Two-Factor Authentication: Add an extra layer of security by enabling two-factor authentication wherever possible.
- Regularly Update Software: Keep your operating system, firewall, and RemoteIoT software up to date to protect against vulnerabilities.
Troubleshooting Common Issues
Issue 1: Connection Problems
If you're experiencing connection issues, check your firewall settings to ensure the necessary ports are open. Additionally, verify that your network is not blocking RemoteIoT traffic.
Issue 2: Slow Performance
Slow performance can be caused by network congestion or misconfigured settings. Optimize your network settings and ensure your Mac has sufficient resources to handle RemoteIoT operations.
Tools and Software Recommendations
Several tools and software can enhance your RemoteIoT experience. Below are some recommendations:
- TunnelBear: A reliable VPN service that can help bypass firewall restrictions.
- Little Snitch: A network monitoring tool for Mac that provides granular control over outgoing connections.
- Wireshark: A powerful network analysis tool for troubleshooting and diagnosing connection issues.
Optimizing Performance
Optimizing the performance of RemoteIoT on your Mac involves several steps, including:
- Minimizing Background Processes: Close unnecessary applications to free up system resources.
- Configuring Network Settings: Adjust your network settings to prioritize RemoteIoT traffic.
- Using a Dedicated Network: If possible, use a dedicated network for RemoteIoT operations to reduce interference.
Conclusion
In conclusion, using RemoteIoT behind a firewall on a Mac is entirely possible with the right configuration and tools. By following the steps outlined in this article, you can ensure secure and efficient access to your IoT devices. Remember to prioritize security and regularly update your systems to protect against potential threats.
We encourage you to leave a comment below sharing your experiences with RemoteIoT or asking any questions you may have. Additionally, feel free to explore other articles on our site for more tips and tricks on managing IoT devices.
References: