In today's interconnected world, managing IoT devices remotely is essential for businesses and individuals alike. However, using RemoteIoT behind a firewall on Mac can pose unique challenges that require a strategic approach. This guide will walk you through the process step-by-step, ensuring you can securely access your IoT devices from anywhere.
Whether you're a network administrator or a tech enthusiast, understanding how to configure RemoteIoT behind a firewall on Mac is crucial for maintaining security and efficiency. In this article, we'll explore the technical aspects, tools, and best practices to help you achieve seamless connectivity.
This guide is designed for users who want to delve into the specifics of RemoteIoT and firewall configurations. By the end of this article, you'll have a solid understanding of how to set up and troubleshoot RemoteIoT on your Mac, even when behind a firewall.
Read also:Deidra Hoffman Net Worth
Table of Contents
- Introduction to RemoteIoT Behind Firewall on Mac
- Understanding Firewalls and Their Role
- Overview of RemoteIoT Technology
- Step-by-Step Setup Guide
- Security Considerations for RemoteIoT
- Troubleshooting Common Issues
- Best Practices for Managing RemoteIoT
- Optimizing Performance
- Tools and Software Recommendations
- Conclusion and Next Steps
Introduction to RemoteIoT Behind Firewall on Mac
RemoteIoT technology enables users to access and manage IoT devices remotely. When working behind a firewall, especially on a Mac, it's essential to understand the nuances of configuring your network for optimal performance and security. Firewalls act as a protective barrier, controlling incoming and outgoing network traffic based on predetermined security rules.
Using RemoteIoT behind a firewall requires a careful balance between accessibility and security. This section will provide an overview of the challenges and solutions associated with setting up RemoteIoT on a Mac device.
By following this guide, you'll learn how to configure your Mac's firewall settings to allow RemoteIoT connections while maintaining robust security protocols.
Understanding Firewalls and Their Role
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Firewalls can be hardware-based, software-based, or a combination of both. They play a critical role in protecting your network from unauthorized access and potential threats.
When using RemoteIoT behind a firewall, it's important to understand how firewalls work and how they can impact your IoT device connectivity. Here are some key points to consider:
- Firewalls can block specific ports or IP addresses to prevent unauthorized access.
- They can be configured to allow or deny traffic based on specific criteria, such as application type or user authentication.
- Firewall rules must be carefully managed to ensure that legitimate RemoteIoT connections are not blocked.
Understanding these principles will help you configure your Mac's firewall settings effectively.
Read also:Fun And Interesting Facts About Rocks
Overview of RemoteIoT Technology
RemoteIoT is a cutting-edge technology that allows users to access and manage IoT devices remotely. It provides a secure and efficient way to interact with connected devices, regardless of their physical location. RemoteIoT technology is widely used in industries such as manufacturing, healthcare, and smart home automation.
Key features of RemoteIoT include:
- Secure data transmission using encryption protocols.
- Real-time monitoring and control of IoT devices.
- Compatibility with a wide range of devices and platforms.
By leveraging RemoteIoT, users can enhance productivity and streamline operations, even when working behind a firewall on a Mac.
Step-by-Step Setup Guide
Configuring Firewall Settings
To use RemoteIoT behind a firewall on Mac, you'll need to configure your firewall settings to allow the necessary connections. Follow these steps:
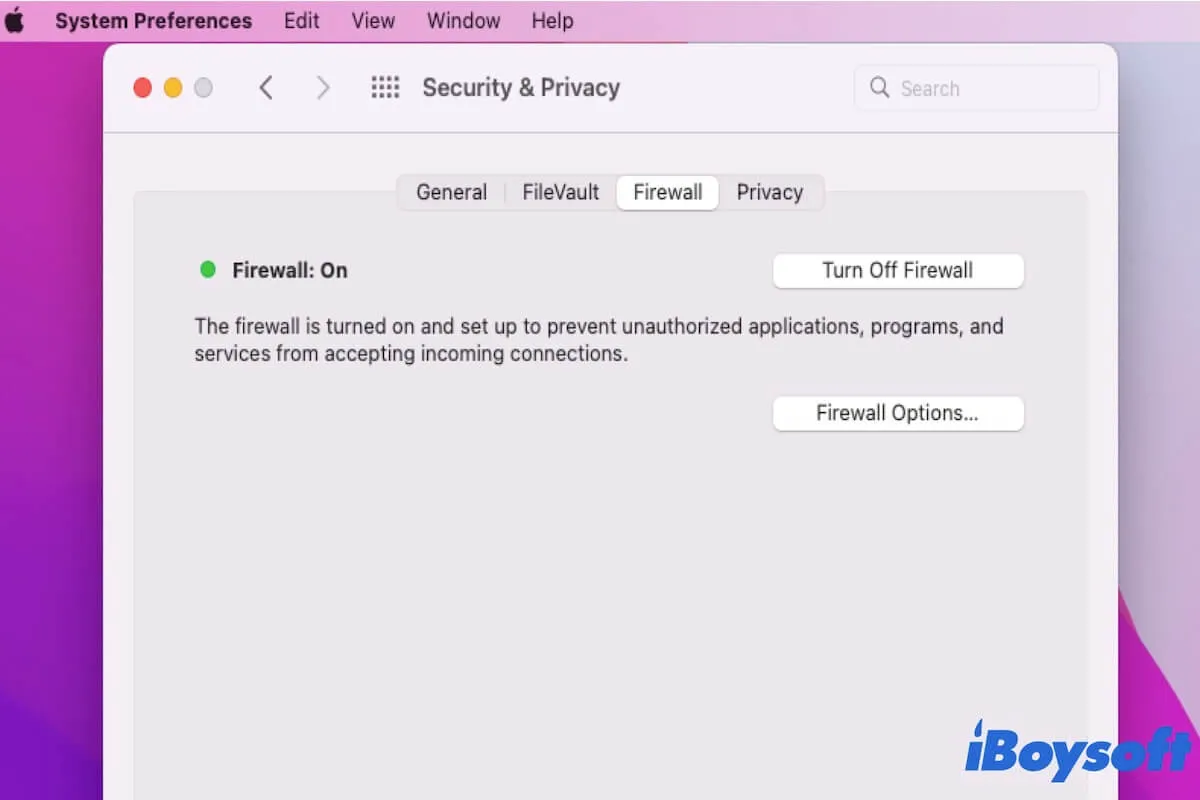
- Open the System Preferences on your Mac and navigate to the Security & Privacy settings.
- Select the Firewall tab and click on the "Turn On Firewall" button.
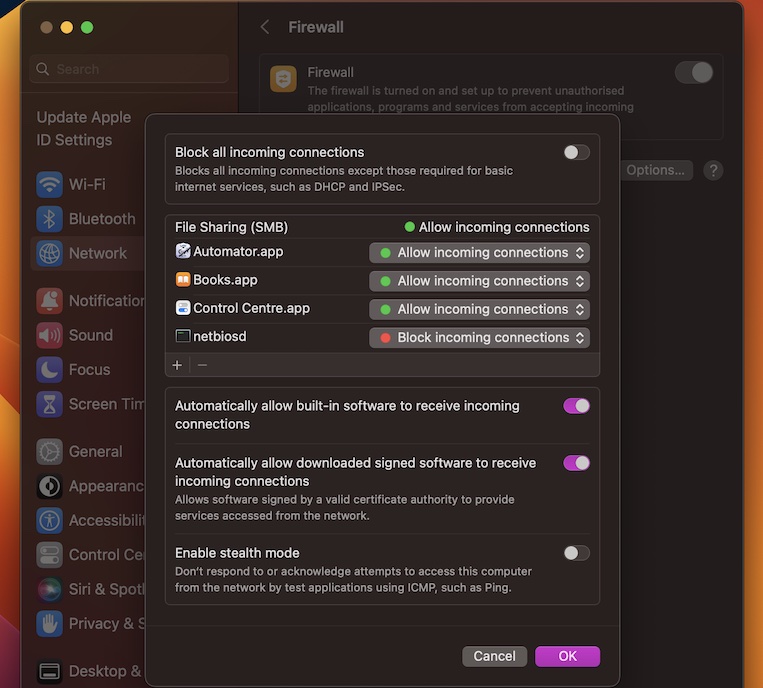
- Click on the "Firewall Options" button to customize your firewall settings.
- Add the RemoteIoT application to the list of allowed applications by clicking the "+" button.
Ensure that the firewall rules are configured to allow traffic on the ports required by RemoteIoT.
Setting Up RemoteIoT
Once your firewall is configured, you can proceed with setting up RemoteIoT on your Mac. Here's how:
- Download and install the RemoteIoT software from the official website.
- Create an account and log in to the RemoteIoT dashboard.
- Connect your IoT devices to the RemoteIoT network.
- Test the connection to ensure that everything is working correctly.
These steps will help you establish a secure and reliable RemoteIoT connection.
Security Considerations for RemoteIoT
Security is paramount when using RemoteIoT behind a firewall. Here are some important considerations to keep in mind:
- Use strong passwords and enable two-factor authentication for added security.
- Regularly update your RemoteIoT software to ensure you have the latest security patches.
- Monitor your network for suspicious activity and configure alerts to notify you of potential threats.
By implementing these security measures, you can protect your IoT devices and data from unauthorized access.
Troubleshooting Common Issues
Even with proper configuration, issues can arise when using RemoteIoT behind a firewall. Here are some common problems and their solutions:
- Connection Issues: Ensure that your firewall rules are correctly configured to allow RemoteIoT traffic.
- Performance Problems: Optimize your network settings and check for bandwidth limitations.
- Authentication Errors: Verify your login credentials and ensure that your account is active.
If you encounter persistent issues, consult the RemoteIoT documentation or contact their support team for assistance.
Best Practices for Managing RemoteIoT
To get the most out of RemoteIoT behind a firewall on Mac, follow these best practices:
- Regularly review and update your firewall rules to ensure they align with your current needs.
- Document your configuration settings and keep them in a secure location for future reference.
- Train your team on the proper use of RemoteIoT and emphasize the importance of security protocols.
By adhering to these best practices, you can maximize the benefits of RemoteIoT while minimizing risks.
Optimizing Performance
Optimizing the performance of RemoteIoT behind a firewall involves several key steps:
- Ensure that your network has sufficient bandwidth to support RemoteIoT traffic.
- Use compression techniques to reduce the size of data transmitted between devices.
- Monitor network performance regularly and make adjustments as needed.
These strategies will help you achieve optimal performance and reliability when using RemoteIoT on your Mac.
Tools and Software Recommendations
Several tools and software can enhance your RemoteIoT experience. Consider using the following:
- Wireshark: A network protocol analyzer that helps you monitor and analyze network traffic.
- Little Snitch: A Mac-specific tool that provides advanced control over outgoing network connections.
- OpenVPN: A secure and reliable solution for creating virtual private networks (VPNs).
These tools can help you troubleshoot issues and optimize your RemoteIoT setup.
Conclusion and Next Steps
In conclusion, using RemoteIoT behind a firewall on Mac requires careful planning and configuration. By following the steps outlined in this guide, you can establish a secure and efficient connection to your IoT devices. Remember to prioritize security, regularly update your settings, and stay informed about the latest developments in RemoteIoT technology.
We encourage you to share your thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our website for more insights into IoT and network security.
References:
![Mac Firewall Setting How To Configure It? [Stepwise Tutorial]](https://techyhost.com/wp-content/uploads/2022/12/changing-firewall-settings-mac-1.jpg)