Remote IoT monitoring via SSH offers a powerful solution for managing and securing devices from afar. In today's interconnected world, Internet of Things (IoT) devices are becoming increasingly popular, driving the need for efficient and secure remote management tools. This article will explore how to set up remote IoT monitoring using SSH on a Mac, along with free software options that enhance your security and control over IoT devices.
As more businesses and individuals adopt IoT technologies, ensuring the security and reliability of these devices has become critical. Remote monitoring via SSH is one of the most secure methods to achieve this goal. By leveraging SSH protocols, users can establish encrypted connections to their IoT devices, ensuring that sensitive data remains protected.
This comprehensive guide will cover everything you need to know about remote IoT monitoring via SSH, including the best free tools available for Mac users. Whether you're a beginner or an advanced user, this article will provide valuable insights into securing your IoT ecosystem.
Read also:Beautiful African Last Names
Table of Contents
- Introduction to Remote IoT Monitoring
- Why Use SSH for IoT Monitoring?
- Mac Support for Remote IoT Monitoring
- Free Tools for Remote IoT Monitoring
- Installation Guide for SSH on Mac
- Configuration Steps for Remote IoT Monitoring
- Security Best Practices for SSH
- Troubleshooting Common Issues
- Performance Optimization Tips
- Future Trends in Remote IoT Monitoring
Introduction to Remote IoT Monitoring
Remote IoT monitoring is the process of managing and maintaining IoT devices from a distance. This method allows users to access, configure, and troubleshoot IoT devices without needing physical access. The ability to remotely monitor IoT devices is essential for businesses and individuals who rely on IoT technology for automation, data collection, and security.
With remote IoT monitoring via SSH, users can establish secure connections to their devices, ensuring that sensitive information remains protected. SSH (Secure Shell) is a cryptographic network protocol that provides secure communication over unsecured networks. By using SSH, users can prevent unauthorized access and data breaches, making it an ideal choice for remote IoT monitoring.
Benefits of Remote IoT Monitoring
- Enhanced security through encrypted connections
- Improved efficiency in managing IoT devices
- Reduced downtime due to faster issue resolution
- Cost savings by eliminating the need for physical site visits
Why Use SSH for IoT Monitoring?
SSH is widely regarded as one of the most secure methods for remote access and management. When it comes to remote IoT monitoring, SSH offers several advantages over other protocols. First and foremost, SSH encrypts all data transmitted between the client and server, ensuring that sensitive information remains protected from unauthorized access.
Another key benefit of SSH is its ability to authenticate users and devices. By using public-key cryptography, SSH ensures that only authorized users can access IoT devices remotely. This adds an extra layer of security, making it difficult for attackers to gain unauthorized access.
Key Features of SSH
- End-to-end encryption for secure communication
- Public-key authentication for secure access
- Support for file transfer and tunneling
Mac Support for Remote IoT Monitoring
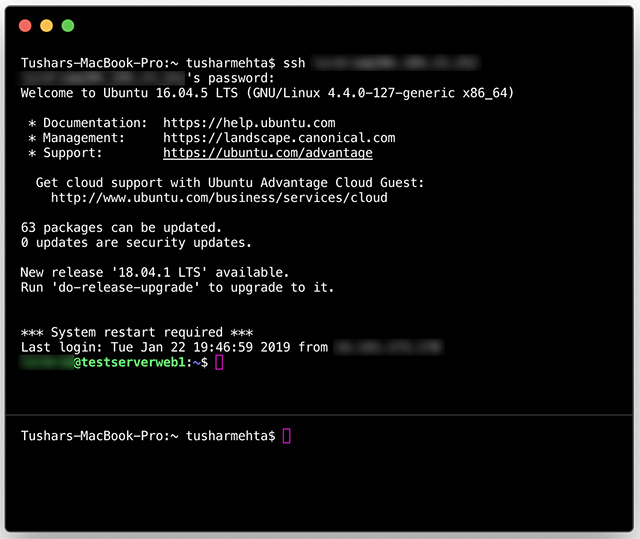
Mac users have access to a wide range of tools and software for remote IoT monitoring via SSH. macOS comes pre-installed with the Terminal application, which includes SSH capabilities. This makes it easy for Mac users to set up and manage SSH connections to their IoT devices without needing additional software.
In addition to the built-in Terminal application, Mac users can also download third-party SSH clients that offer advanced features and a more user-friendly interface. These tools can help simplify the process of remote IoT monitoring, making it accessible to users of all skill levels.
Read also:Hip Hop Playlist Names
Popular SSH Clients for Mac
- Terminal (built-in macOS application)
- PuTTY (cross-platform SSH client)
- MobaXterm (advanced SSH client with additional features)
Free Tools for Remote IoT Monitoring
There are several free tools available for remote IoT monitoring via SSH. These tools offer a range of features and capabilities, making it easy for users to find the right solution for their needs. Below are some of the most popular free tools for remote IoT monitoring:
1. OpenSSH
OpenSSH is an open-source implementation of the SSH protocol. It is widely used for secure remote access and management of IoT devices. OpenSSH is available on most Unix-based operating systems, including macOS, making it a popular choice for Mac users.
2. PuTTY
PuTTY is a free and open-source SSH client that supports multiple platforms, including macOS. It offers a simple and intuitive interface, making it easy for users to establish secure connections to their IoT devices.
Installation Guide for SSH on Mac
Installing SSH on a Mac is a straightforward process. Since macOS comes pre-installed with the Terminal application, which includes SSH capabilities, users can begin using SSH without needing additional software. Below is a step-by-step guide to setting up SSH on a Mac:
- Open the Terminal application on your Mac.
- Type "ssh" followed by the username and IP address of the IoT device you wish to connect to. For example:
ssh username@192.168.1.100. - Enter your password when prompted to establish the connection.
Alternative Installation Methods
For users who prefer a graphical interface, third-party SSH clients such as PuTTY or MobaXterm can be downloaded and installed on their Mac. These clients offer additional features and a more user-friendly interface, making them ideal for users who are new to SSH.
Configuration Steps for Remote IoT Monitoring
Once SSH is installed and configured, users can begin setting up remote IoT monitoring. Below are the key steps involved in configuring SSH for remote IoT monitoring:
- Enable SSH on the IoT device you wish to monitor.
- Generate SSH keys for secure authentication.
- Set up port forwarding if necessary to access the IoT device from outside the local network.
- Test the connection to ensure that SSH is working correctly.
Tips for Configuring SSH
- Use strong passwords and enable two-factor authentication for added security.
- Regularly update SSH software to ensure that you have the latest security patches.
- Monitor SSH logs for suspicious activity and take action if necessary.
Security Best Practices for SSH
While SSH is a secure protocol, it is important to follow best practices to ensure that your remote IoT monitoring setup remains protected. Below are some key security best practices for SSH:
- Use strong, unique passwords for SSH authentication.
- Enable public-key authentication to eliminate the need for passwords.
- Disable root login to prevent attackers from gaining administrative access.
- Limit SSH access to specific IP addresses or subnets.
Additional Security Measures
In addition to the above best practices, users can also implement additional security measures such as:
- Using firewalls to restrict SSH access.
- Enabling intrusion detection systems to monitor for suspicious activity.
- Regularly auditing SSH configurations and logs.
Troubleshooting Common Issues
Even with proper configuration, users may encounter issues when setting up remote IoT monitoring via SSH. Below are some common issues and their solutions:
1. Connection Refused
This issue typically occurs when the SSH service is not running on the IoT device. To resolve this, ensure that SSH is enabled and running on the device.
2. Authentication Failed
This issue may occur if the username or password is incorrect. Double-check the credentials and ensure that public-key authentication is properly configured.
3. Connection Timeout
This issue may occur if the IoT device is not reachable from the network. Check the network settings and ensure that port forwarding is configured correctly if necessary.
Performance Optimization Tips
To ensure optimal performance when using SSH for remote IoT monitoring, users can implement the following tips:
- Use compression to reduce data transfer times.
- Limit the number of simultaneous SSH connections to prevent overloading the IoT device.
- Use a wired connection instead of Wi-Fi for improved stability and speed.
Advanced Performance Tips
For advanced users, additional performance optimizations can be achieved by:
- Tuning SSH parameters in the configuration file.
- Using SSH multiplexing to reuse existing connections.
- Implementing load balancing for large-scale IoT deployments.
Future Trends in Remote IoT Monitoring
As IoT technology continues to evolve, so too will the methods used for remote monitoring. Future trends in remote IoT monitoring via SSH may include:
- Increased use of artificial intelligence and machine learning for predictive maintenance.
- Integration with cloud-based platforms for enhanced scalability and flexibility.
- Improved security features to address emerging threats and vulnerabilities.
By staying informed about these trends, users can ensure that their remote IoT monitoring setups remain up-to-date and secure.
Conclusion
Remote IoT monitoring via SSH offers a secure and efficient solution for managing IoT devices from afar. By following the steps outlined in this article, Mac users can set up and configure SSH for remote IoT monitoring using free tools and software. Remember to follow best practices for security and performance to ensure that your IoT ecosystem remains protected and optimized.
We invite you to share your thoughts and experiences with remote IoT monitoring in the comments section below. Additionally, feel free to explore our other articles for more insights into IoT technology and security. Thank you for reading!