As technology continues to evolve, the ability to access IoT devices remotely has become increasingly important. However, navigating the complexities of firewalls and network security can be a daunting task for many users. If you're looking to use RemoteIoT behind a firewall on your Mac, this guide will walk you through every step of the process. Whether you're a beginner or an advanced user, you'll find valuable insights here to help you achieve seamless remote connectivity.
RemoteIoT technology allows users to control and monitor IoT devices from virtually anywhere. However, firewalls often act as barriers, restricting unauthorized access to your network. This article aims to demystify the process of setting up RemoteIoT behind a firewall on a Mac, ensuring that you can maintain secure and efficient connections without compromising your network's integrity.
By following the steps outlined in this guide, you'll gain a deeper understanding of how firewalls function, the tools you need, and the best practices for setting up RemoteIoT securely. Whether you're managing smart home devices, industrial equipment, or any other IoT-enabled system, this guide will empower you to take full control.
Read also:How Much Does Jim Parsons Make On Young Sheldon
Table of Contents
- Introduction to RemoteIoT
- Understanding Firewalls
- Setting Up RemoteIoT on Mac
- Configuring Firewall Settings
- Using Port Forwarding
- Securing Your Connection
- Troubleshooting Common Issues
- Advanced Techniques
- Best Practices for RemoteIoT
- Conclusion
Introduction to RemoteIoT
RemoteIoT refers to the ability to access and control IoT devices remotely, even when they're located behind a firewall or within a private network. This technology is essential for anyone who wants to manage IoT devices without being physically present. Whether you're a homeowner managing smart appliances or an IT professional overseeing industrial equipment, RemoteIoT offers flexibility and convenience.
When using RemoteIoT behind a firewall on a Mac, it's crucial to understand the underlying mechanisms that enable secure communication. Firewalls are designed to protect networks by filtering incoming and outgoing traffic based on predefined rules. To ensure that your RemoteIoT setup works seamlessly, you'll need to configure your firewall settings and employ strategies like port forwarding and secure tunneling.
Why Use RemoteIoT?
- RemoteIoT allows you to monitor and control devices from anywhere in the world.
- It enhances productivity by eliminating the need for physical presence.
- It provides real-time data access, enabling timely decision-making.
Understanding Firewalls
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It acts as a barrier between your internal network and external threats, ensuring that only authorized traffic is allowed to pass through. Firewalls are essential for protecting sensitive data and preventing unauthorized access.
When using RemoteIoT behind a firewall, you'll need to configure your firewall to allow specific types of traffic. This involves setting up rules that permit communication between your Mac and the IoT devices you want to control. By understanding how firewalls work, you can ensure that your RemoteIoT setup remains secure and functional.
Types of Firewalls
- Packet Filtering Firewalls: Analyze individual packets and decide whether to allow or block them.
- Stateful Inspection Firewalls: Monitor active connections and use this information to make decisions about traffic.
- Application-Level Gateways: Operate at the application layer and provide advanced security features.
Setting Up RemoteIoT on Mac
Before you can use RemoteIoT behind a firewall, you'll need to set it up on your Mac. This involves installing the necessary software, configuring network settings, and ensuring that your IoT devices are properly connected. Here's a step-by-step guide to help you get started:
Step 1: Install RemoteIoT Software
Download and install the RemoteIoT software on your Mac. Make sure to choose the version that's compatible with your operating system. Follow the installation instructions carefully, and restart your Mac if prompted.
Read also:Andrea Espada Sexy Pics
Step 2: Connect IoT Devices
Ensure that all your IoT devices are connected to the same network as your Mac. This can usually be done through Wi-Fi or Ethernet. Check the device manuals for specific connection instructions.
Step 3: Test the Connection
Once everything is set up, test the connection between your Mac and the IoT devices. Use the RemoteIoT software to send commands and verify that the devices respond as expected.
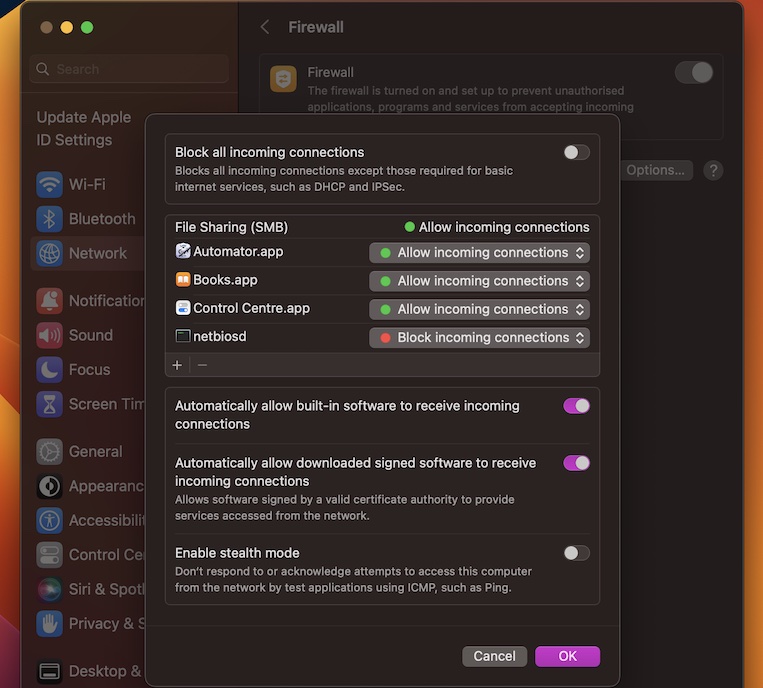
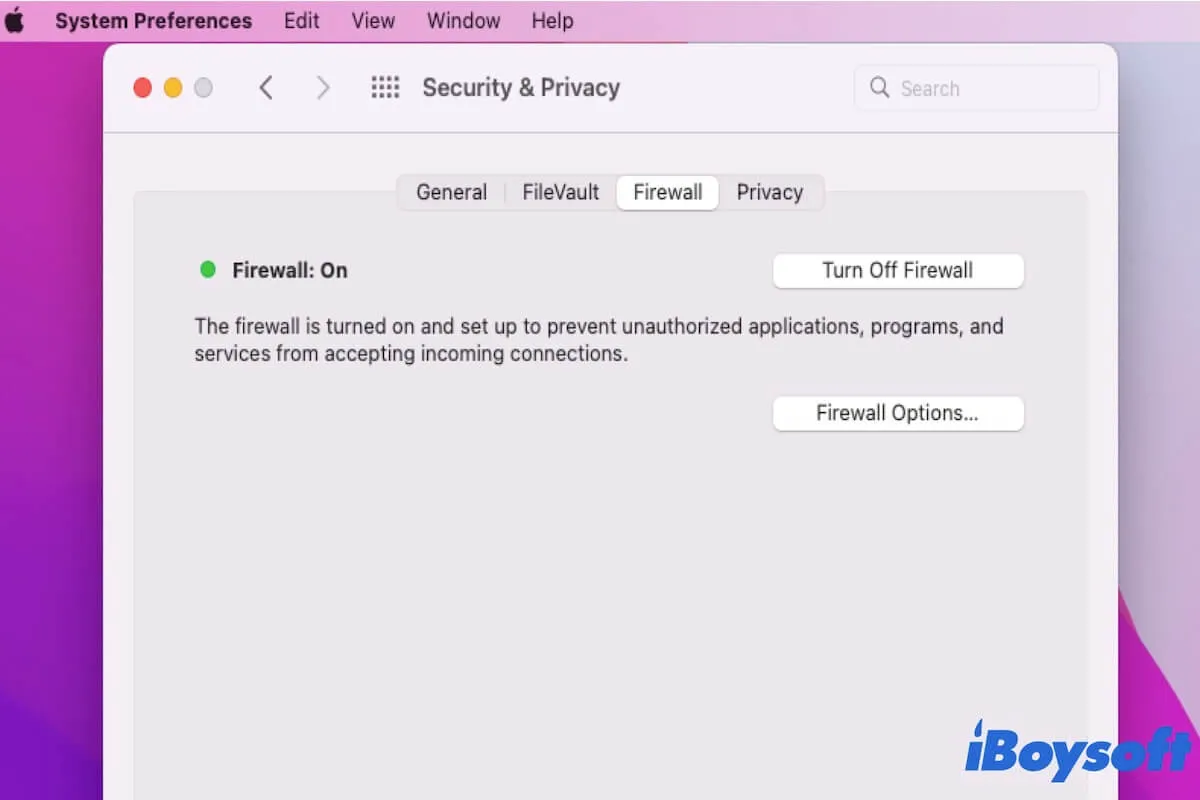
Configuring Firewall Settings
Configuring your firewall is a critical step in setting up RemoteIoT behind a firewall. By default, firewalls block most types of incoming traffic to protect your network. To allow RemoteIoT to function properly, you'll need to create specific rules that permit the necessary traffic.
Identifying Required Ports
Each IoT device may require different ports to function correctly. Check the device documentation to determine which ports need to be opened. Common ports used by IoT devices include:
- Port 80 (HTTP)
- Port 443 (HTTPS)
- Port 22 (SSH)
Creating Firewall Rules
Log in to your firewall's management interface and create rules that allow traffic on the required ports. Be sure to specify the source and destination IP addresses to ensure that only authorized devices can communicate.
Using Port Forwarding
Port forwarding is a technique that allows external devices to access devices within your local network. By forwarding specific ports to your Mac, you can enable RemoteIoT to function even when behind a firewall.
Steps to Set Up Port Forwarding
- Access your router's configuration page using its IP address.
- Locate the port forwarding section and add a new rule.
- Specify the external port, internal IP address, and internal port.
- Save the changes and test the connection.
Securing Your Connection
Security should always be a top priority when setting up RemoteIoT behind a firewall. By implementing strong security measures, you can protect your network and devices from unauthorized access.
Use Strong Authentication
Ensure that all devices and services require strong passwords or multi-factor authentication. Avoid using default credentials and change them regularly.
Encrypt Your Data
Use encryption protocols like SSL/TLS to secure data transmissions between your Mac and IoT devices. This ensures that sensitive information remains protected from interception.
Troubleshooting Common Issues
Even with careful setup, issues can arise when using RemoteIoT behind a firewall. Here are some common problems and their solutions:
Issue: Devices Not Responding
Solution: Verify that the firewall rules are correctly configured and that the required ports are open. Restart the devices and try again.
Issue: Slow Connection
Solution: Check your network bandwidth and ensure that there are no bottlenecks. Optimize your firewall settings to prioritize RemoteIoT traffic.
Advanced Techniques
For users seeking more advanced control over their RemoteIoT setup, there are several techniques that can enhance functionality and security:
Use a Virtual Private Network (VPN)
A VPN creates a secure tunnel between your Mac and the IoT devices, ensuring that all communications remain encrypted and private.
Implement Network Segmentation
Segregate your IoT devices into a separate network to minimize the risk of unauthorized access to other parts of your network.
Best Practices for RemoteIoT
To ensure a successful and secure RemoteIoT setup, follow these best practices:
- Regularly update your software and firmware to protect against vulnerabilities.
- Monitor network activity to detect and respond to suspicious behavior.
- Document your configuration settings for easy reference and troubleshooting.
Conclusion
Using RemoteIoT behind a firewall on a Mac is a powerful way to manage IoT devices remotely while maintaining network security. By following the steps outlined in this guide, you can set up a secure and efficient RemoteIoT system that meets your needs. Remember to prioritize security, regularly update your systems, and stay informed about the latest developments in IoT technology.
We encourage you to share your thoughts and experiences in the comments section below. If you found this guide helpful, consider sharing it with others who may benefit from it. For more information on IoT and network security, explore our other articles on the site.
References:
- https://www.cisco.com/c/en/us/products/security/firewalls/what-is-a-firewall.html
- https://www.cloudflare.com/learning/security/glossary/what-is-port-forwarding/
- https://www.paloaltonetworks.com/cyberpedia/what-is-a-vpn
![Mac Firewall Setting How To Configure It? [Stepwise Tutorial]](https://techyhost.com/wp-content/uploads/2022/12/changing-firewall-settings-mac-1.jpg)